Customizable Templates is a feature of Identity Verification software that allows users to create their own templates for verifying an individual's identity. This can be useful for businesses that need to verify the identity of their employees or customers. Still, it can also be used by individuals who want to verify their identity.
There are two ways to use Customizable Templates you can either create your own template or you can download a pre-made template from the internet. To create your own template, you must enter information about the individual's name, date of birth, Social Security number, and other identifying information. Once you have entered this information, you must select a method to verify the individual's identity. The most common methods are government-issued ID documents such as a driver's license or passport or biometric data such as fingerprints or iris scans.
If you download a pre-made template, you will likely find many options available. These templates typically include fields for the same information you would need to enter if creating your own template; however, they may include additional fields specifically designed for identity verification purposes. For example, some templates may ask questions about the individual's employment history or educational background to verify their identity more thoroughly.
Once you have created or downloaded a Customizable Template, using it is relatively simple just print out the document and have the individual fill out all required fields. After completing everything correctly (including providing any necessary supporting documentation), simply sign and date the document yourself and keep it on file for future reference should any problems arise.
The best thing about this feature is that it allows businesses and individuals to tailor the identity verification process to their specific needs. Whether you need to verify the identity of just a few employees or customers or you want to be able to verify the identities of everyone who comes into contact with your business, Customizable Templates make it easy to do so.
There are a few potential downsides to using this feature, however. First, if you create your own template, there is always the possibility that you may forget something important or make a mistake when entering information. Additionally, if you download a pre-made template from the internet, there is no guarantee that it will be 100% accurate; after all, anyone can create these templates, and not all of them will have been thoroughly vetted for accuracy.
Finally, while Customizable Templates can save businesses and individuals time in the short term by allowing them to quickly verify someone's identity without having to request supporting documentation (such as a driver's license or passport), in the long term, they may end up causing more problems than they solve if an individual's identity is later called into question. Still, there is no record of them ever having used the Customizable Template.

 Lightico provides a complete solution for end-to-end digital identity verification, from collecting customer data to verifying their identity.
Lightico provides a complete solution for end-to-end digital identity verification, from collecting customer data to verifying their identity. The verification process is based on a proprietary algorithm that compares the photo and the face of the person.
The verification process is based on a proprietary algorithm that compares the photo and the face of the person.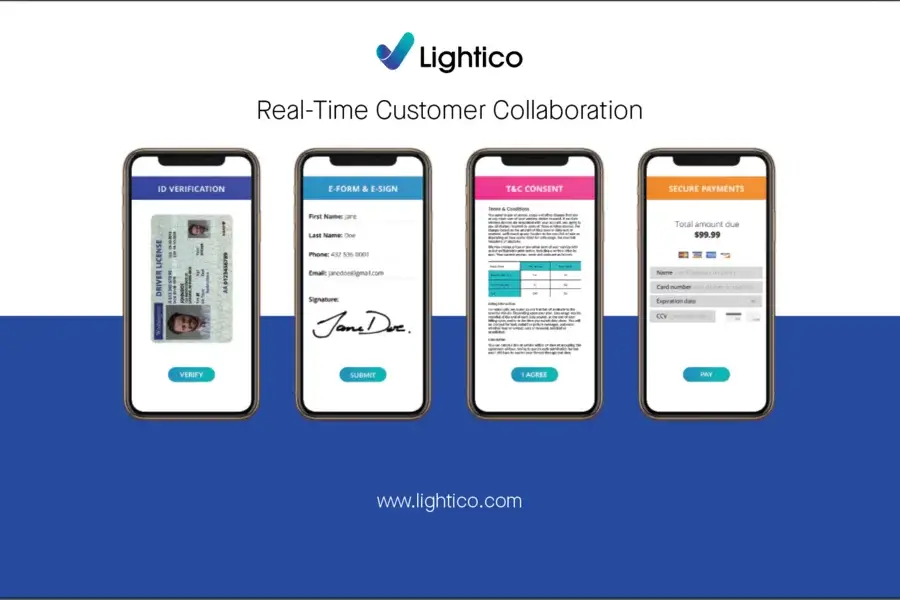 A trusted technology partner with multi-layered security infrastructure.
A trusted technology partner with multi-layered security infrastructure.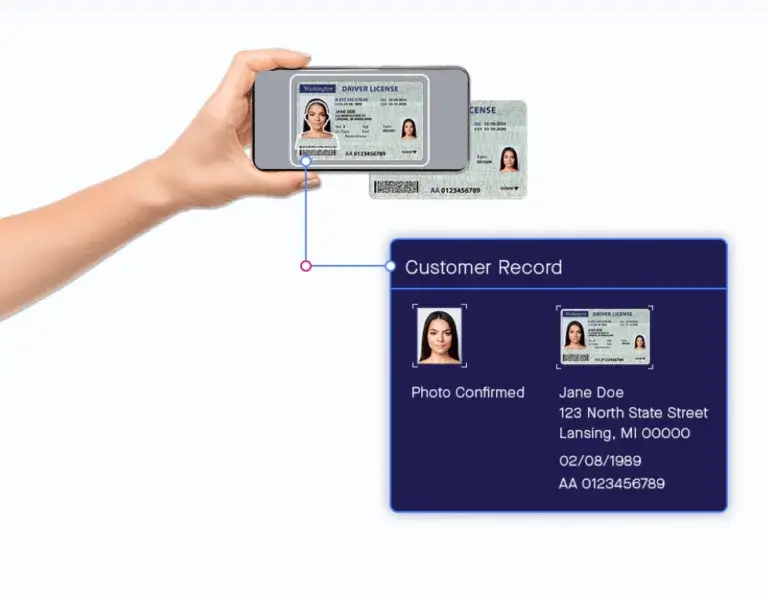 Verifying someone who they say they are remotely has never been more important.
Verifying someone who they say they are remotely has never been more important.
 Instig provides the best OCR technology to digitize and automate identity verification process.
Instig provides the best OCR technology to digitize and automate identity verification process.  You can verify your ID at any time and any place.
You can verify your ID at any time and any place. Enable your site or app with real-time ID scanning and recognition.
Enable your site or app with real-time ID scanning and recognition.
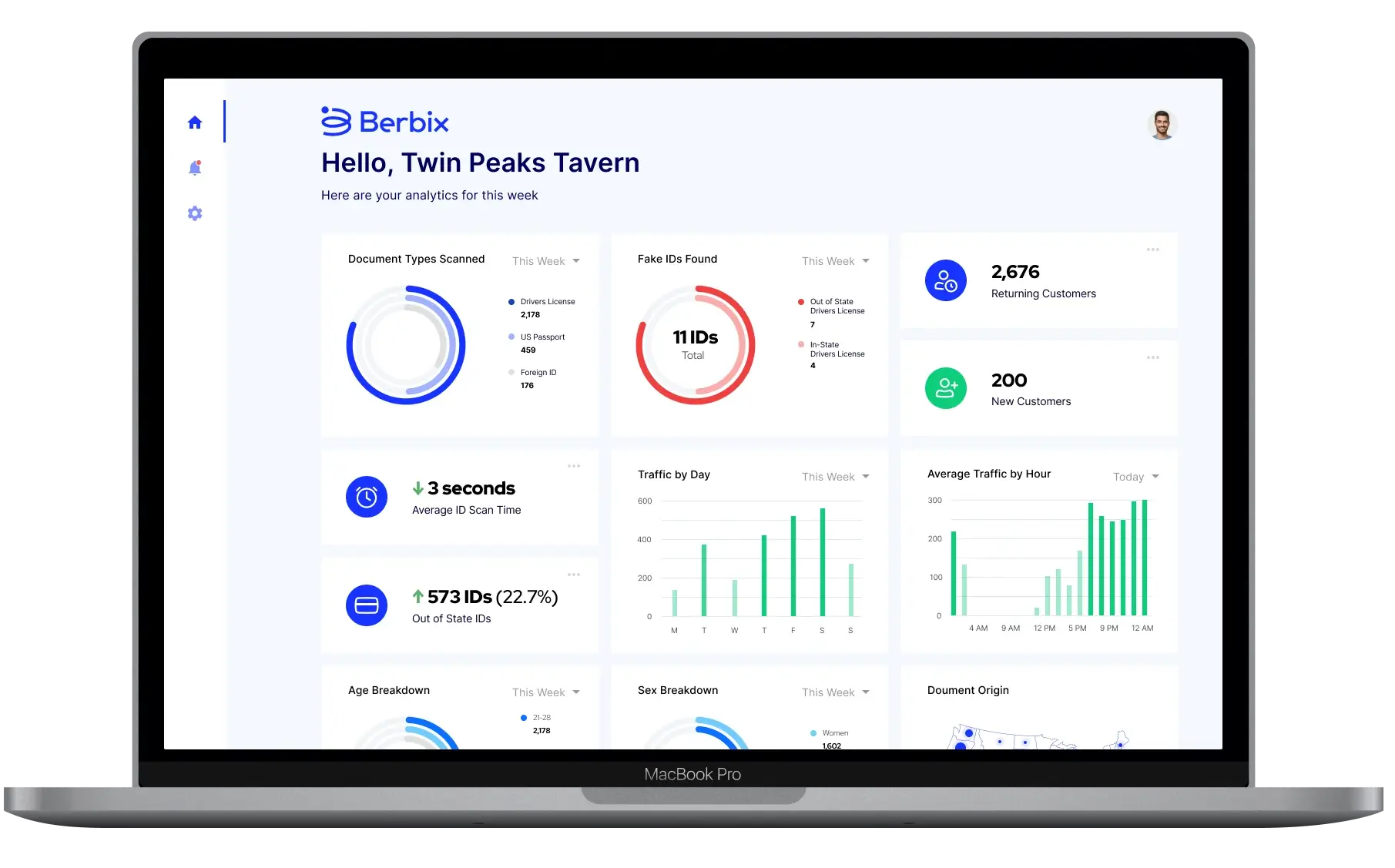 Integrate Berbix with your existing systems to verify documents and scan ID with the highest degree of accuracy and speed to make better business decisions.
Integrate Berbix with your existing systems to verify documents and scan ID with the highest degree of accuracy and speed to make better business decisions. This report is accessible from the Transactions section of your Berbix dashboard.
This report is accessible from the Transactions section of your Berbix dashboard.
 Add SheerID verification to your e-commerce workflow to initiate eligibility checks based on your program’s criteria.
Add SheerID verification to your e-commerce workflow to initiate eligibility checks based on your program’s criteria. You can make it even harder for fraudsters to abuse your discount by implementing email loop requiring unique email address.
You can make it even harder for fraudsters to abuse your discount by implementing email loop requiring unique email address. Prevent discount fraud with SheerID's digital verification.
Prevent discount fraud with SheerID's digital verification.
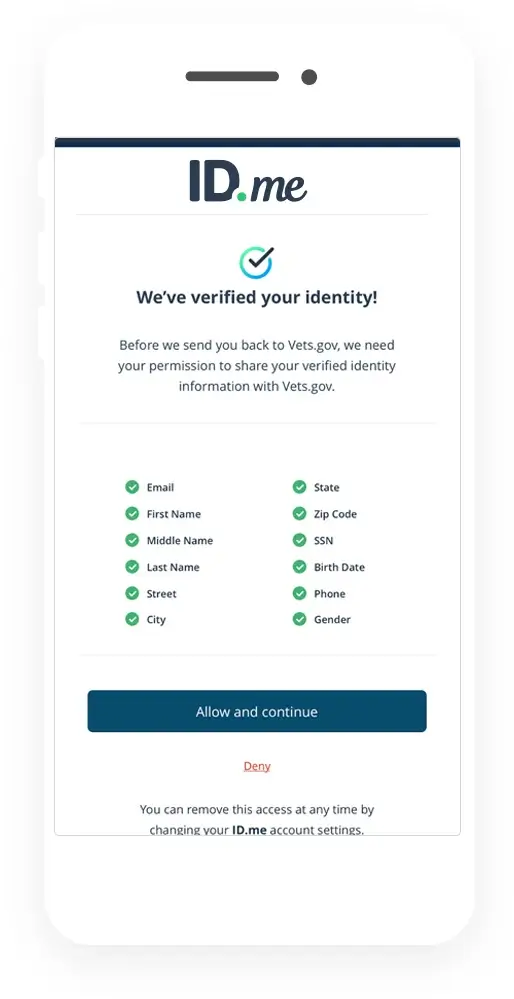 ID.me provides identity proofing, authentication and community verification for organizations across sectors.
ID.me provides identity proofing, authentication and community verification for organizations across sectors. An easy way to add extra layer of security without adding too much friction for users.
An easy way to add extra layer of security without adding too much friction for users.
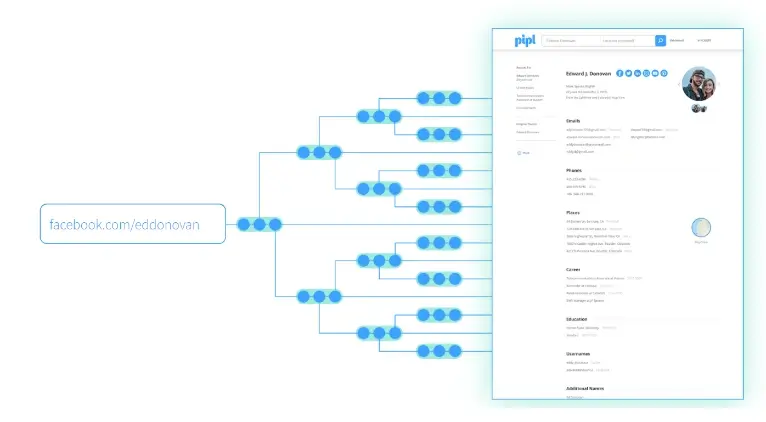 With Pipl's proprietary clustering algorithms, you are assured to deliver highly accurate identity profiles instantly.
With Pipl's proprietary clustering algorithms, you are assured to deliver highly accurate identity profiles instantly.
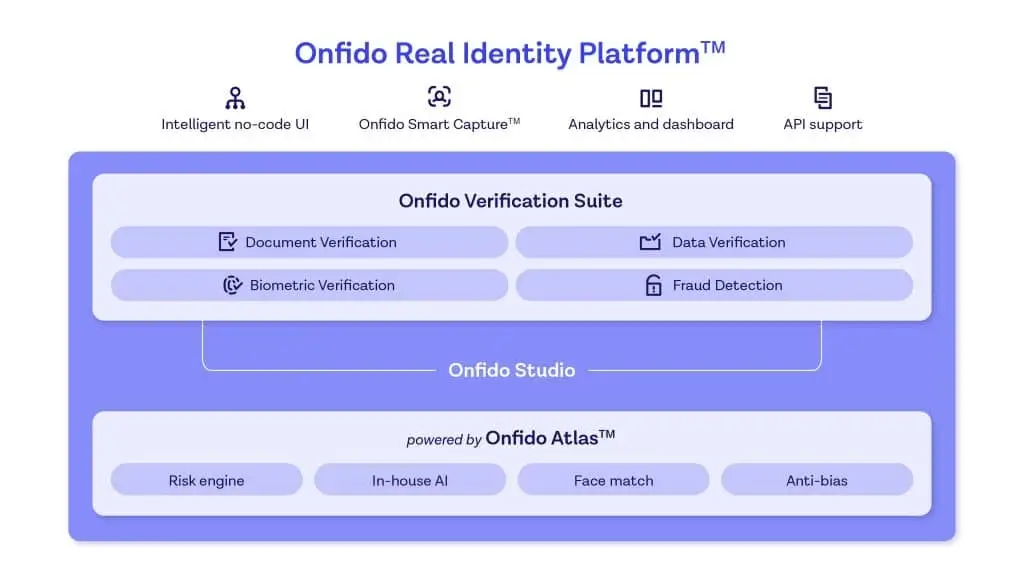 Onfido is a leading global identity verification provider, with expanded biometrics and AI fraud threat mitigation platform capabilities.
Onfido is a leading global identity verification provider, with expanded biometrics and AI fraud threat mitigation platform capabilities.
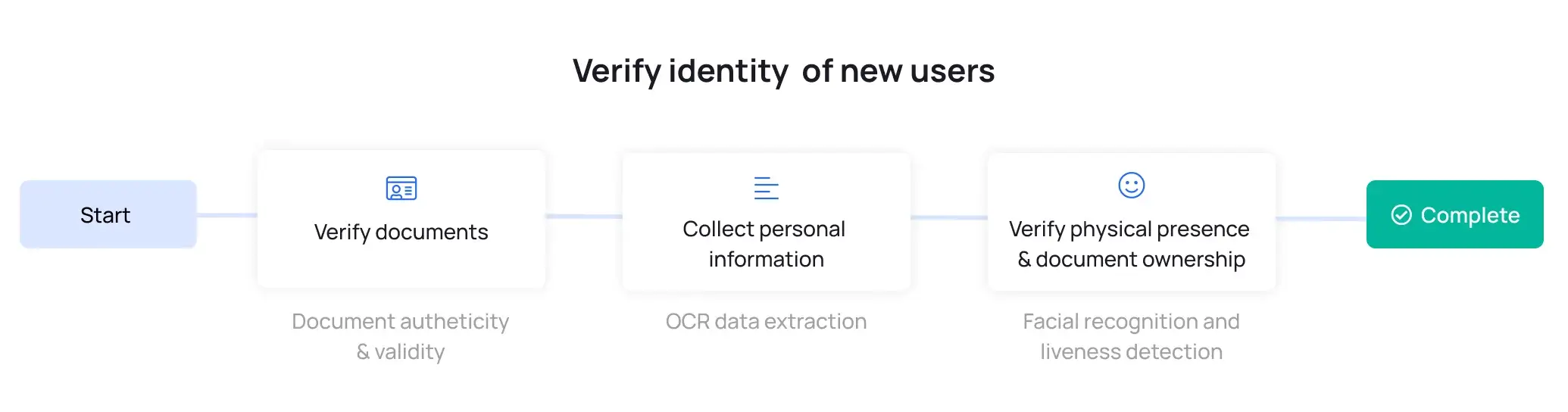 Instantly verify consumers and business entities online with Trulioo's automated identity verification.
Instantly verify consumers and business entities online with Trulioo's automated identity verification.
 Verify your customer’s account details and ownership in seconds.
Verify your customer’s account details and ownership in seconds.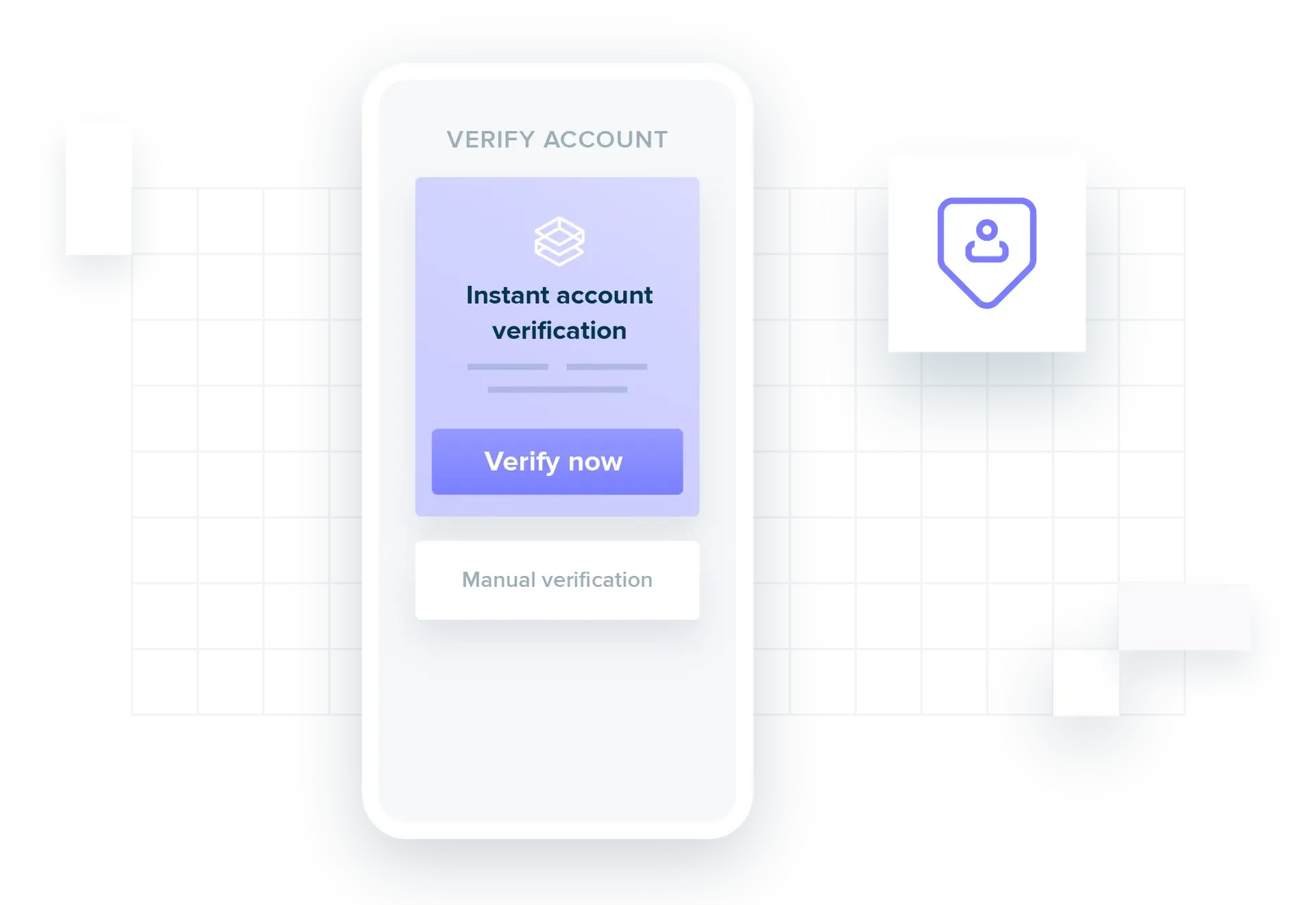 Slash your fraud risk with automated checks through a single API call.
Slash your fraud risk with automated checks through a single API call. An extra layer of security is used to verify the identity of someone logging into an account.
An extra layer of security is used to verify the identity of someone logging into an account.
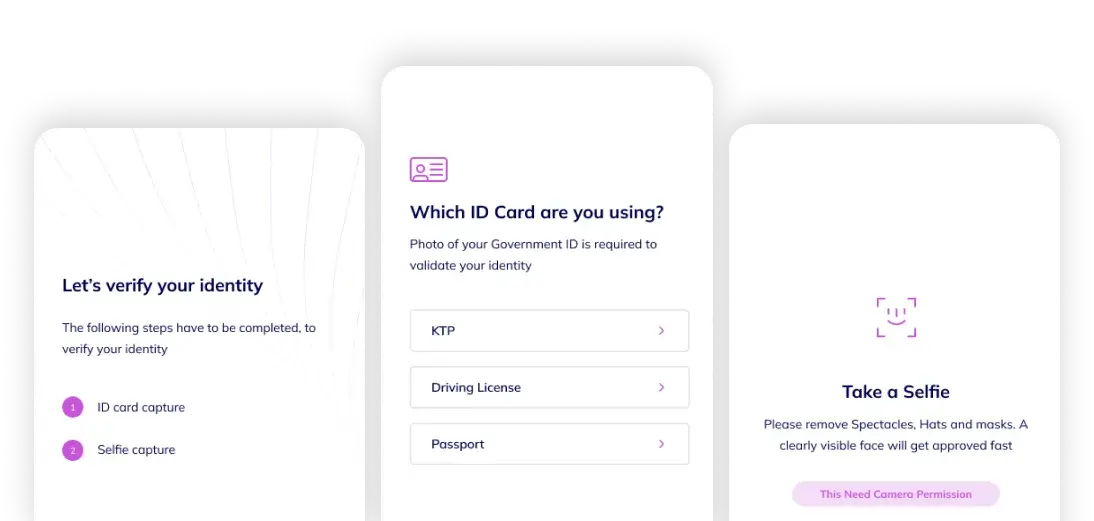 With Hyperverge's proprietary AI technology, you have the ability to innovate fast and add custom AI checks as new needs are identified.
With Hyperverge's proprietary AI technology, you have the ability to innovate fast and add custom AI checks as new needs are identified.
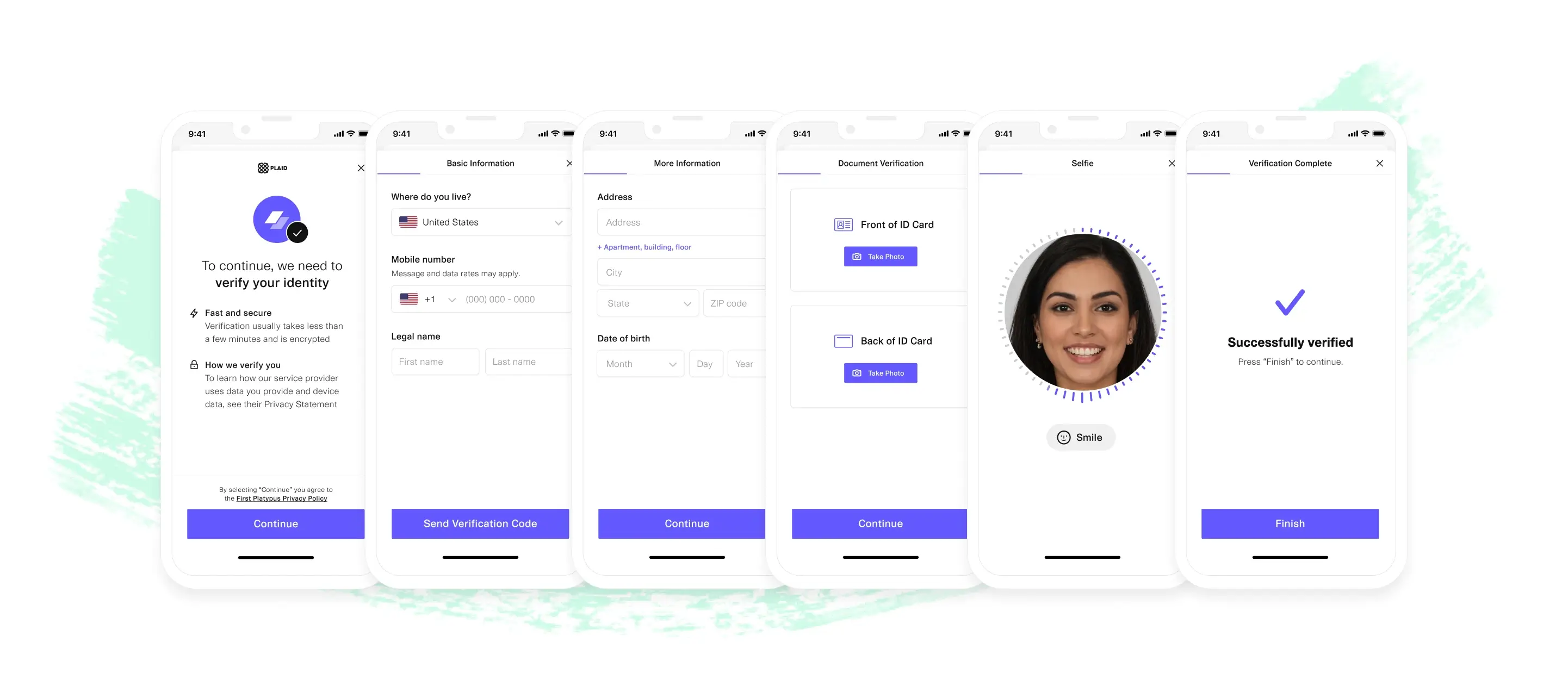 Verify identities in as little as 30 seconds with Plaid's easy and conversion-optimized experience providing a frictionless experience for your customers.
Verify identities in as little as 30 seconds with Plaid's easy and conversion-optimized experience providing a frictionless experience for your customers. Verify your customers wherever they are with a single solution.
Verify your customers wherever they are with a single solution.
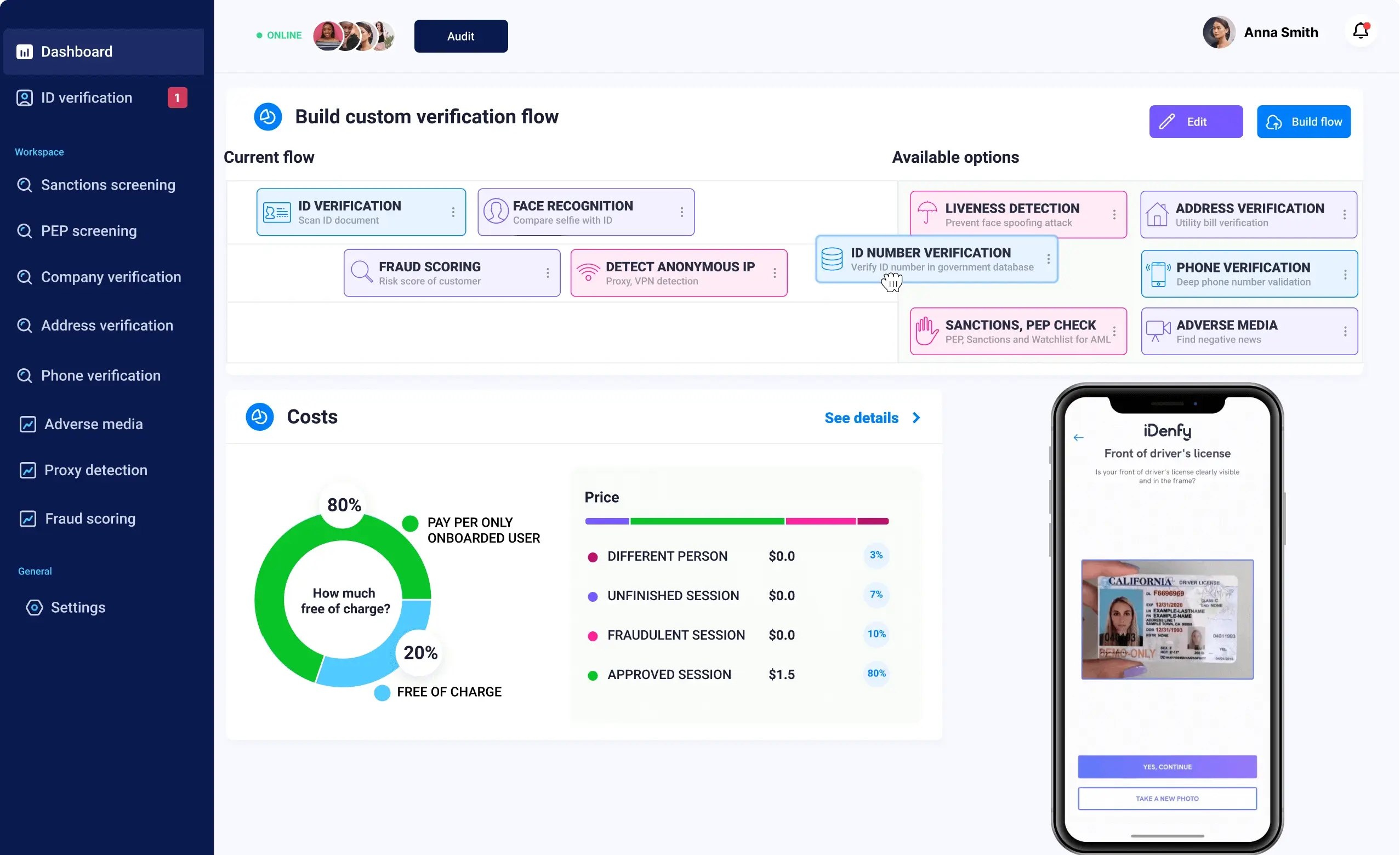 Idenfy has a proprietary identity verification software that is 100% compliant with GDPR, CCPA, and all other latest data protection laws.
Idenfy has a proprietary identity verification software that is 100% compliant with GDPR, CCPA, and all other latest data protection laws. With 2FA regulatory security as an additional fraud prevention tool.
With 2FA regulatory security as an additional fraud prevention tool.
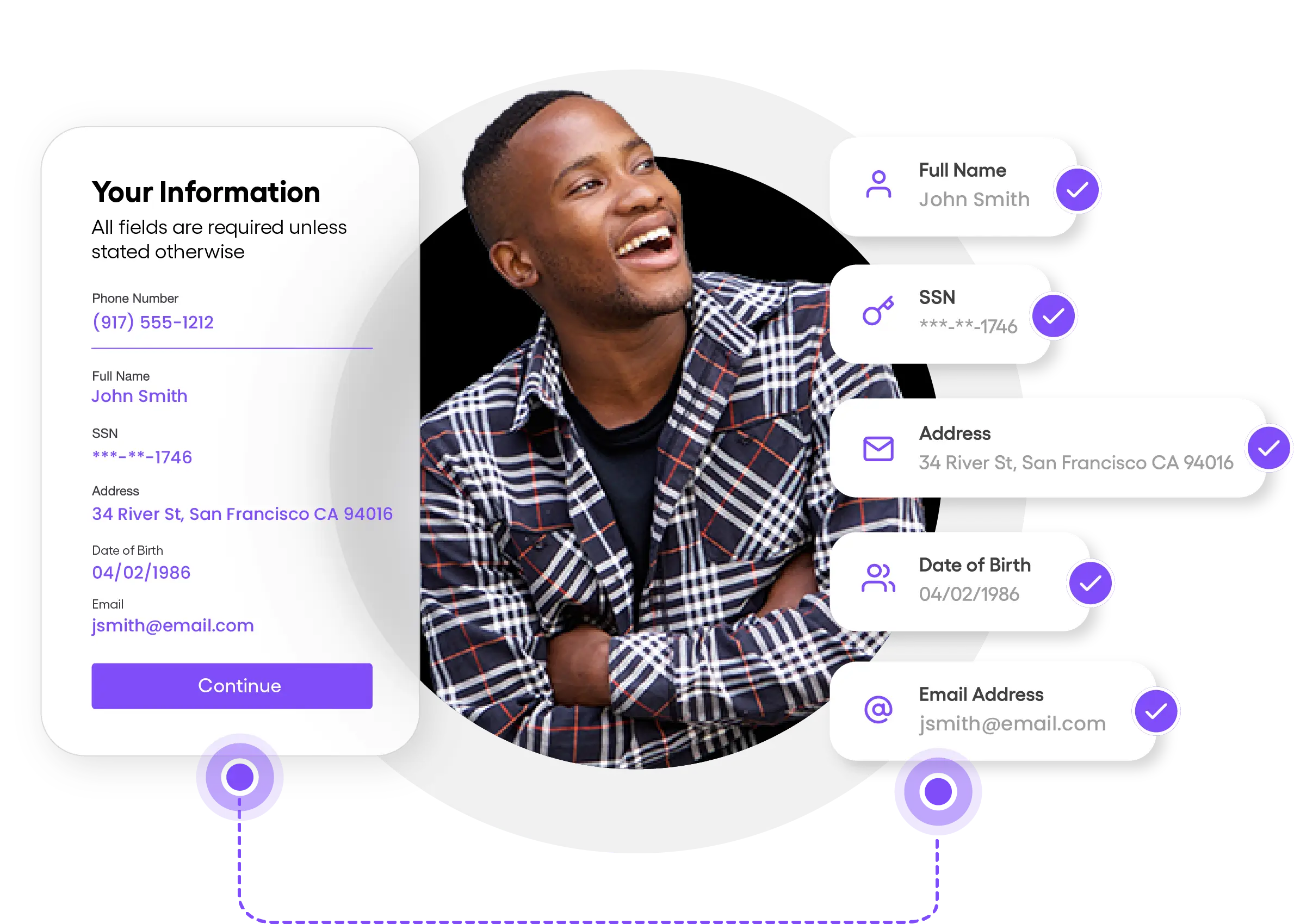 From onboarding to ongoing verification, Prove offers an unparalleled identity verification solution.
From onboarding to ongoing verification, Prove offers an unparalleled identity verification solution.
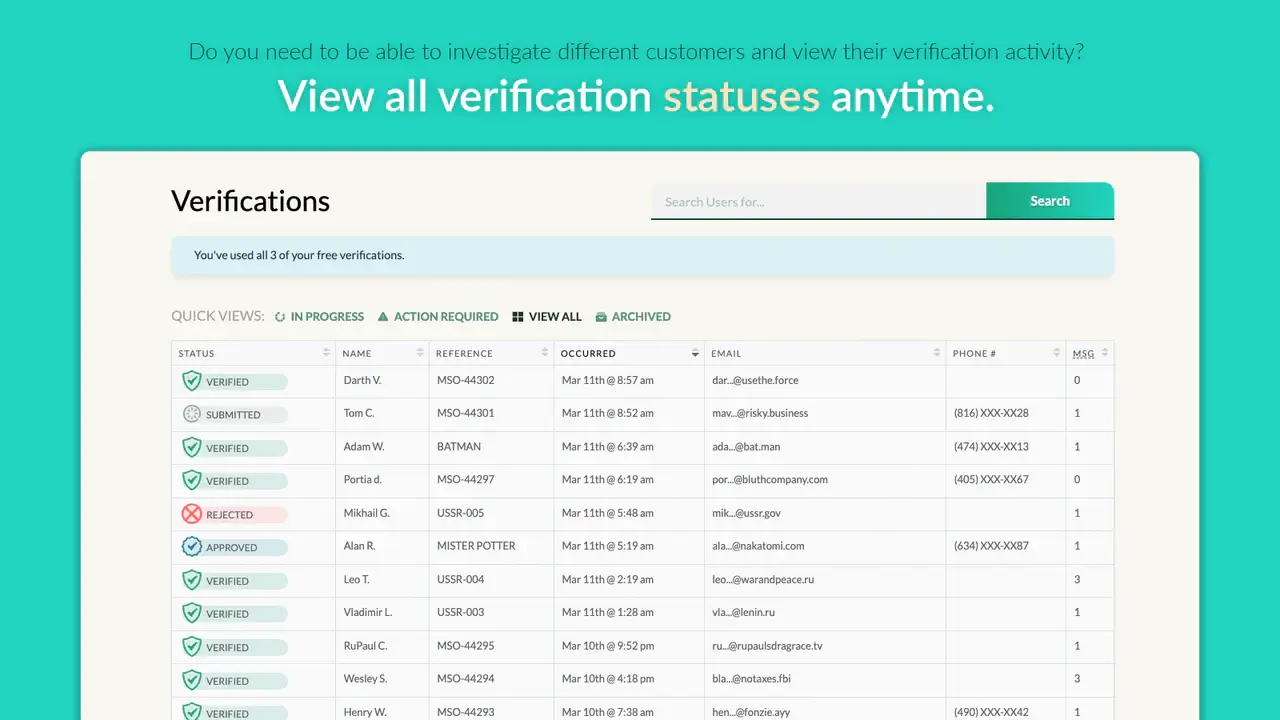 Verify people with ease, prevent fraud, and meet KYC and AML compliance guidelines with Token of Trust identity verification.
Verify people with ease, prevent fraud, and meet KYC and AML compliance guidelines with Token of Trust identity verification. With 2FA enabled, you have an extra layer of security.
With 2FA enabled, you have an extra layer of security. Validate the ownership of an identity with a biometric screening of a selfie.
Validate the ownership of an identity with a biometric screening of a selfie.
 Quickly and automatically verify the digital identities of new customers and existing users with Jumio’s identity proofing and eKYC solutions.
Quickly and automatically verify the digital identities of new customers and existing users with Jumio’s identity proofing and eKYC solutions. Thwart fraudsters with Jumio’s identity verification process.
Thwart fraudsters with Jumio’s identity verification process.
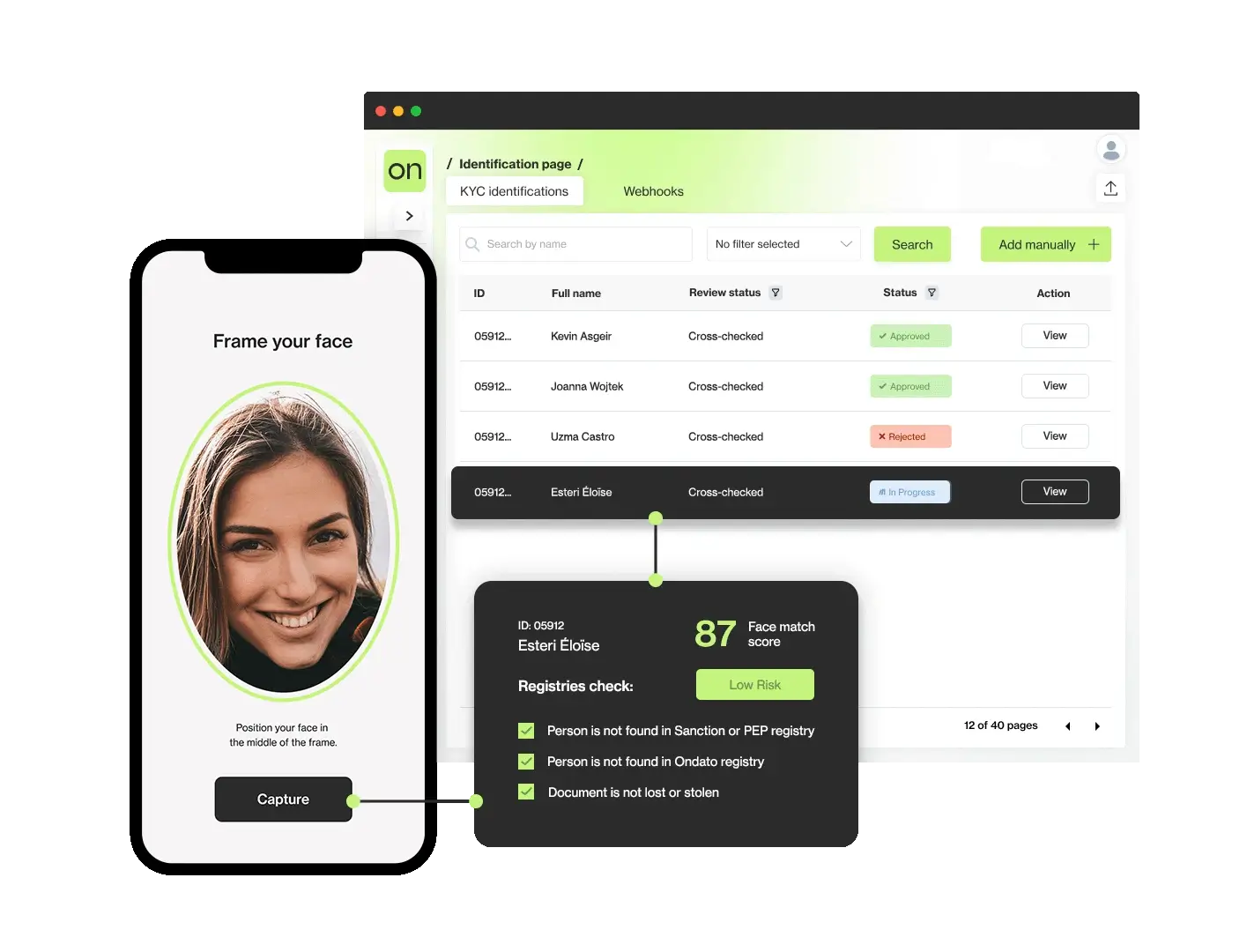 Automated identity verification that significantly helps digital services.
Automated identity verification that significantly helps digital services. A simple solution but secure method with SMS message.
A simple solution but secure method with SMS message.
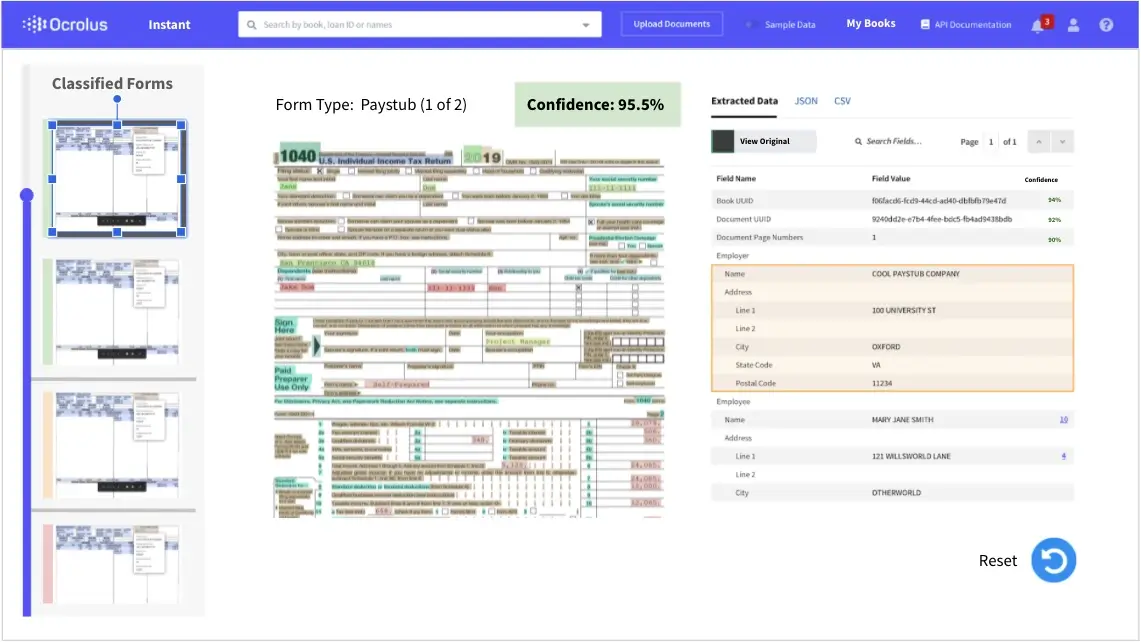 Ocrolus is a turnkey solution for document-driven workflows in the digital age providing modern document analysis infrastructure.
Ocrolus is a turnkey solution for document-driven workflows in the digital age providing modern document analysis infrastructure.
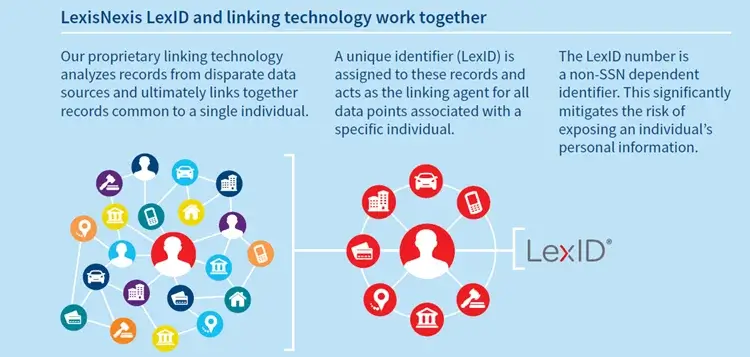 A unique identifier for patient record matching and interoperability.
A unique identifier for patient record matching and interoperability.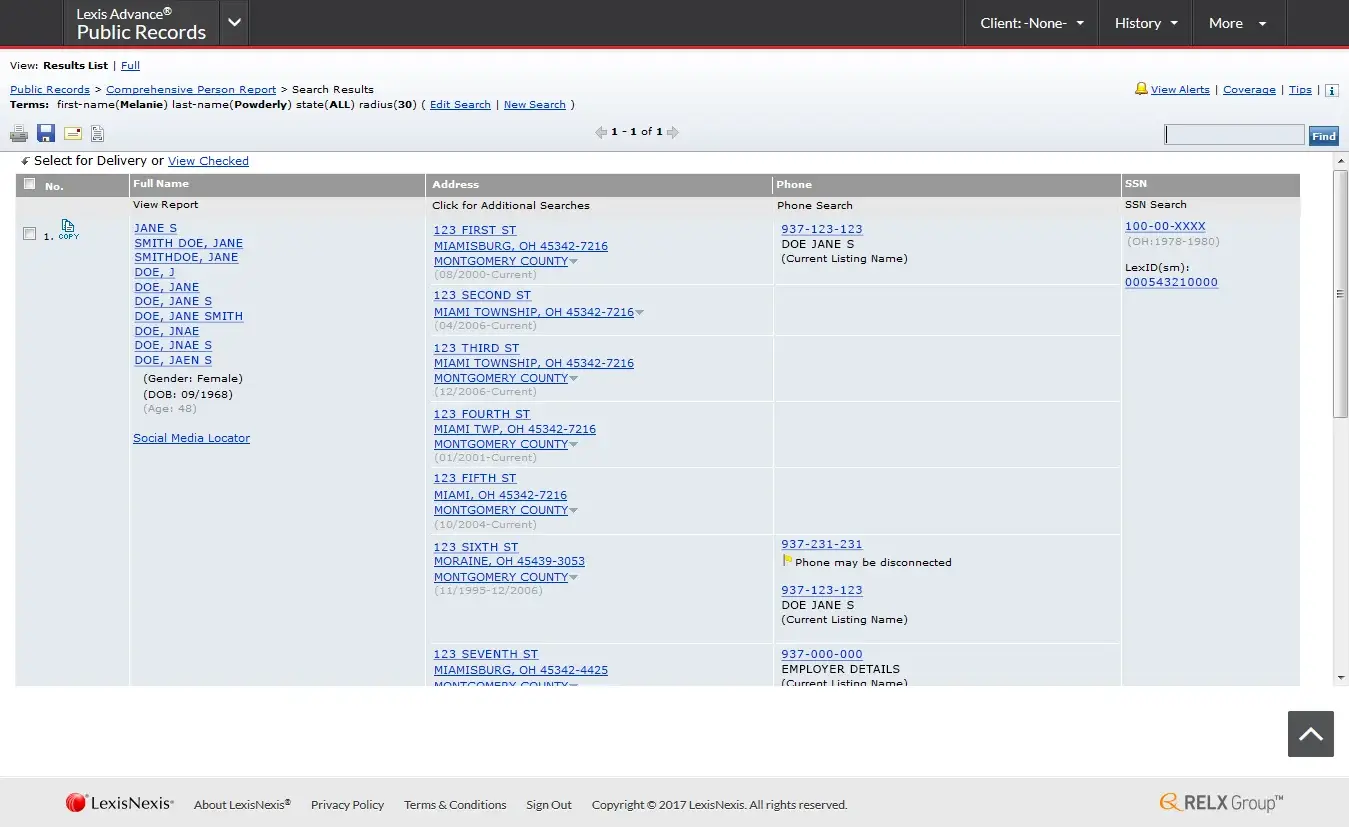 Get the latest records with LexisNexis dynamic collection including historical information stored n public records.
Get the latest records with LexisNexis dynamic collection including historical information stored n public records.
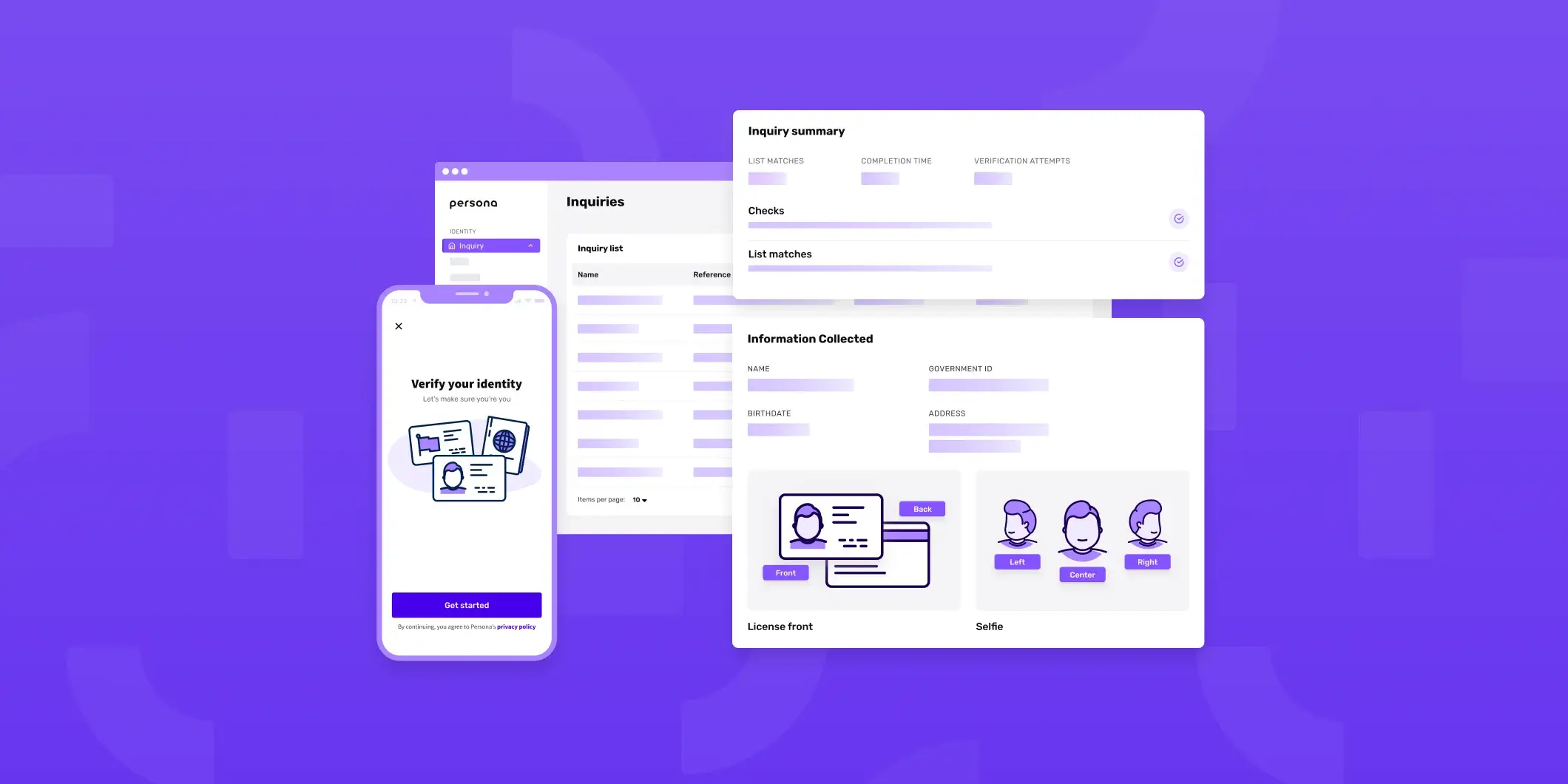 Tackle identity challenges head-on with Persona's identity infrastructure.
Tackle identity challenges head-on with Persona's identity infrastructure.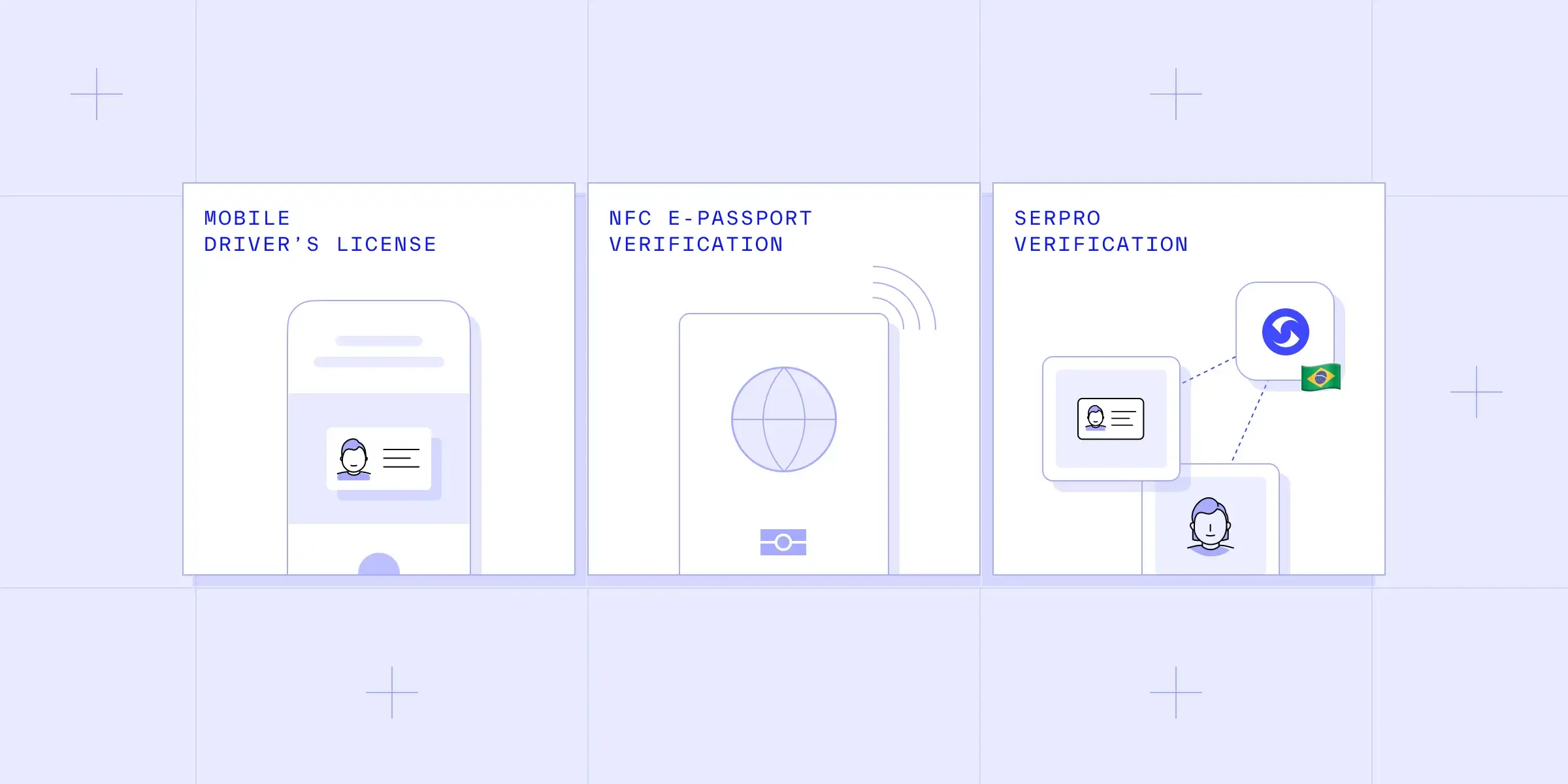 A streamlined interface and intuitive verification process to verify user details in seconds.
A streamlined interface and intuitive verification process to verify user details in seconds. Using sophisticated algorithms that analyze a variety of data, Persona has the ability to detect whether a sensor is viewing a live biometric sample.
Using sophisticated algorithms that analyze a variety of data, Persona has the ability to detect whether a sensor is viewing a live biometric sample.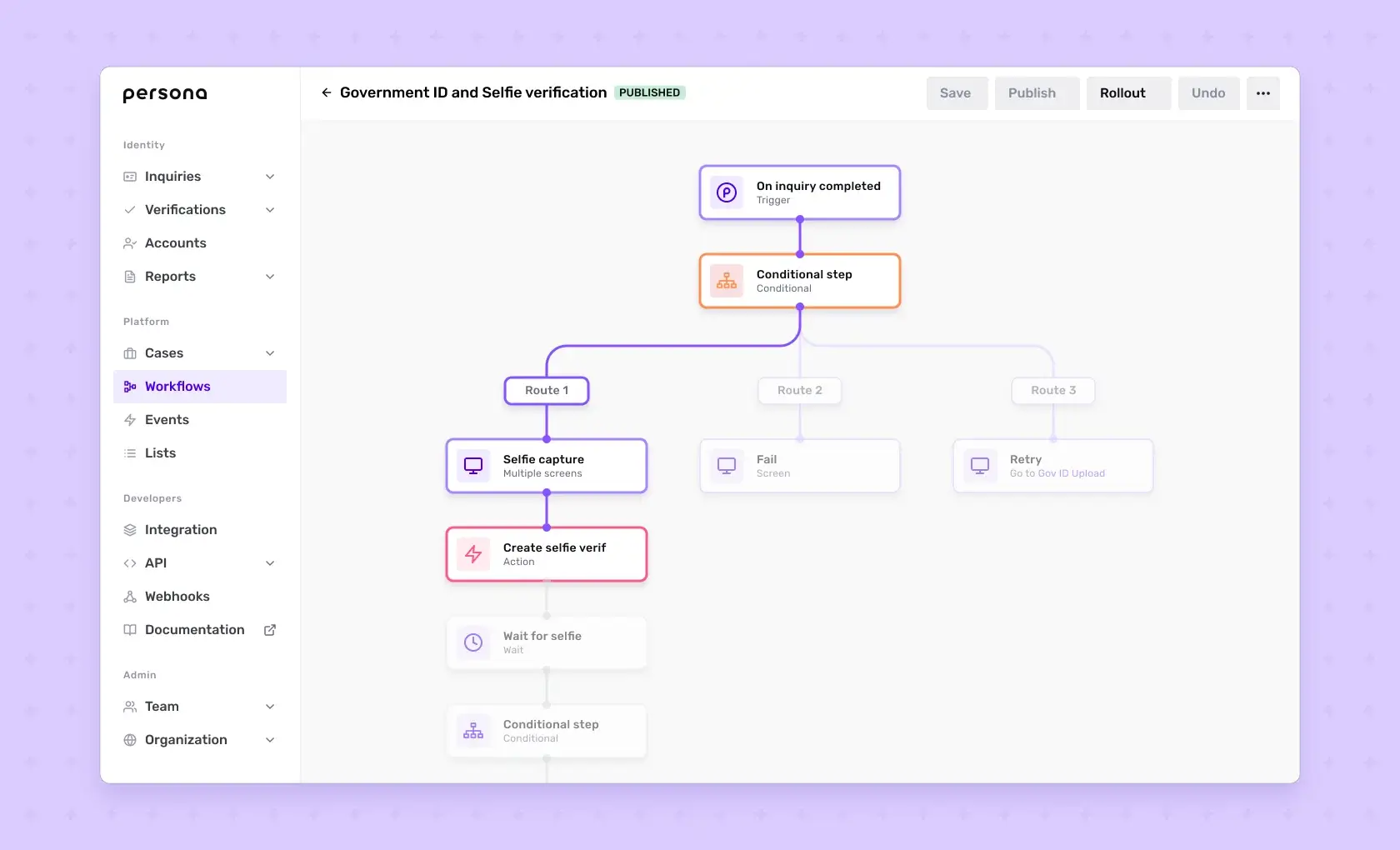 Customize workflow to your heart's content. Drag and drop to see what works for you.
Customize workflow to your heart's content. Drag and drop to see what works for you.
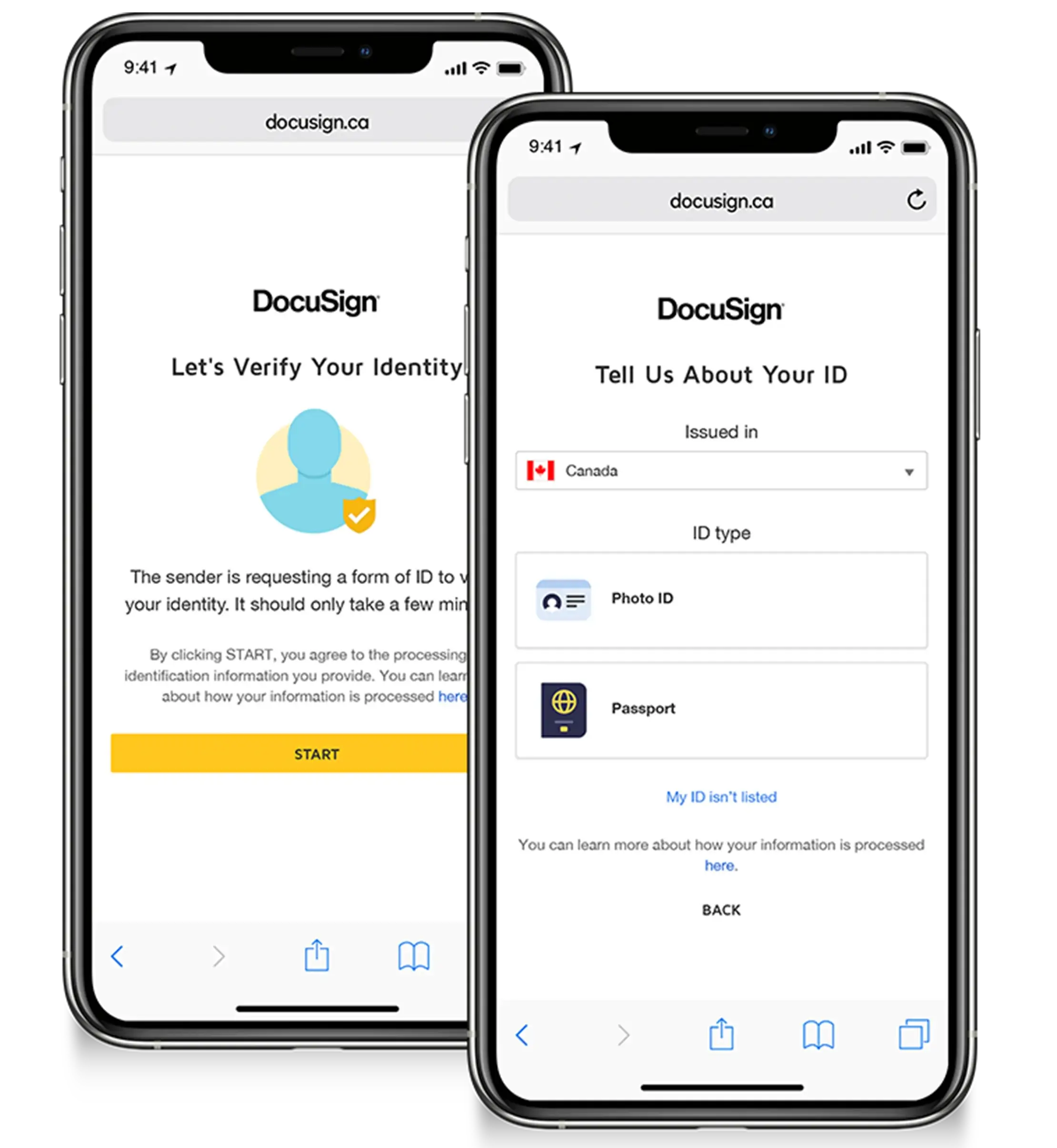 DocuSign ID Verification supports government photo IDs and European eIDs by automating identification anytime.
DocuSign ID Verification supports government photo IDs and European eIDs by automating identification anytime.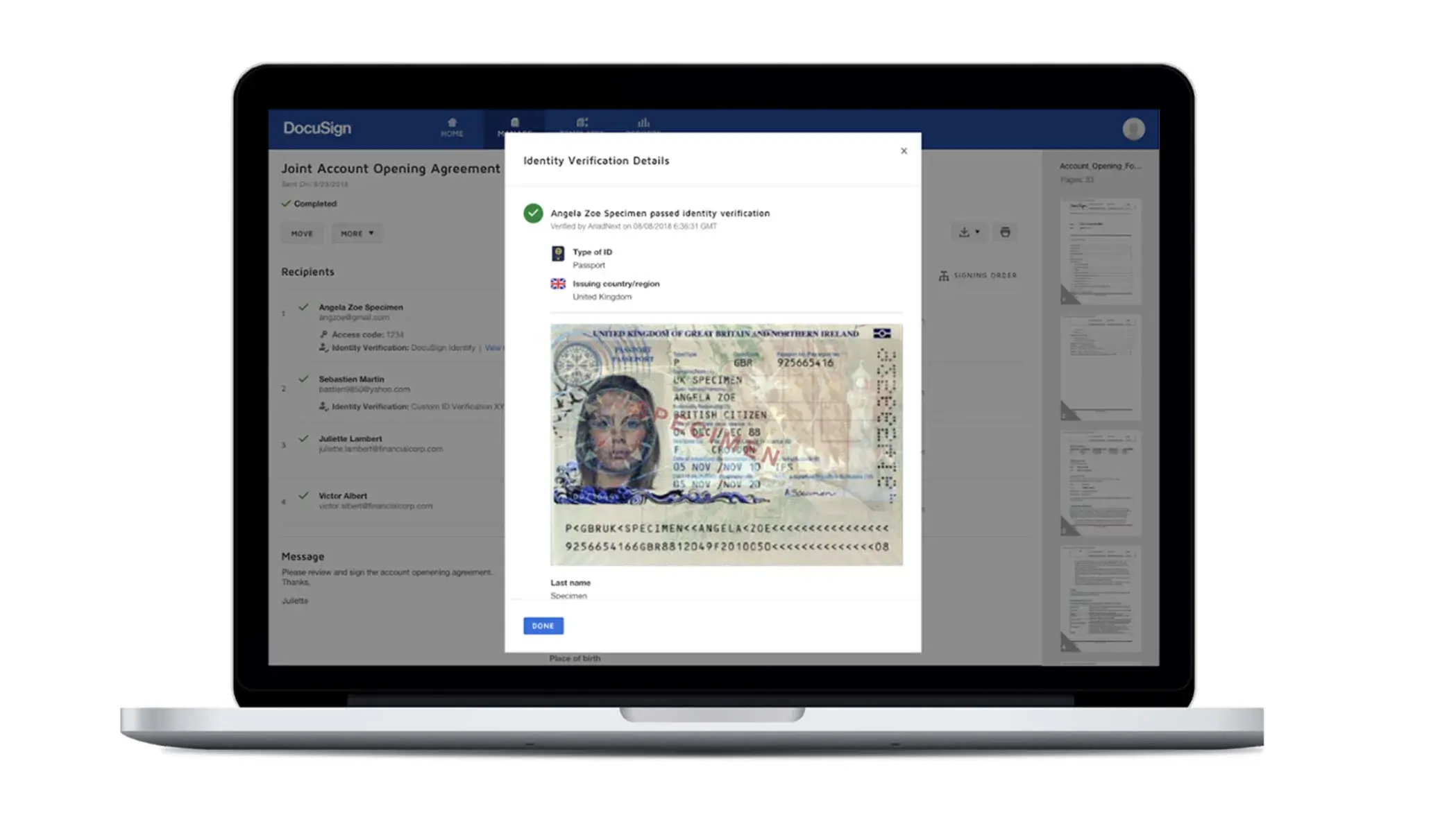 DocuSign Identify provides identity proofing and authentication to verify signer.
DocuSign Identify provides identity proofing and authentication to verify signer. An integration that streamlines the time it takes for organizations to onboard brand-new employees.
An integration that streamlines the time it takes for organizations to onboard brand-new employees. DocuSign prioritizes the safety and security of your Agreement experience through signer verification.
DocuSign prioritizes the safety and security of your Agreement experience through signer verification.
 Provides its user AI-based ID verification and automated anomaly detection.
Provides its user AI-based ID verification and automated anomaly detection.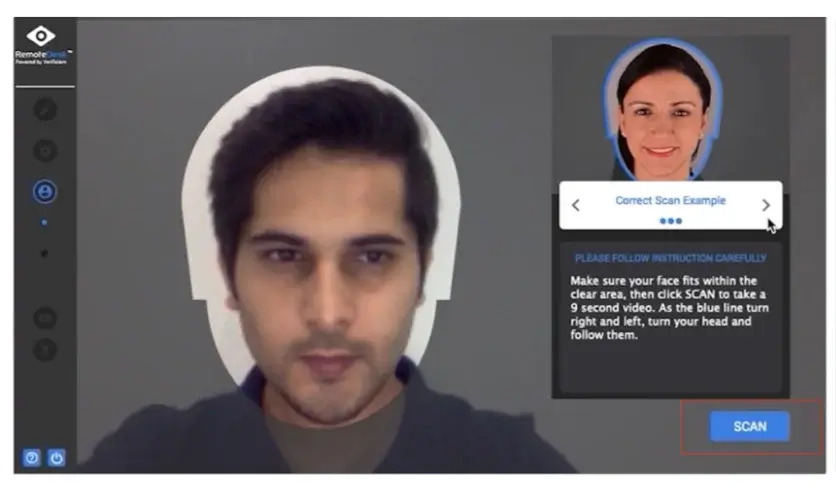 RemoteDesk verifies the identities of employees, ensuring user authentication.
RemoteDesk verifies the identities of employees, ensuring user authentication.
 Emptor's platform is built to leverage artificial intelligence for a seamless identity verification.
Emptor's platform is built to leverage artificial intelligence for a seamless identity verification.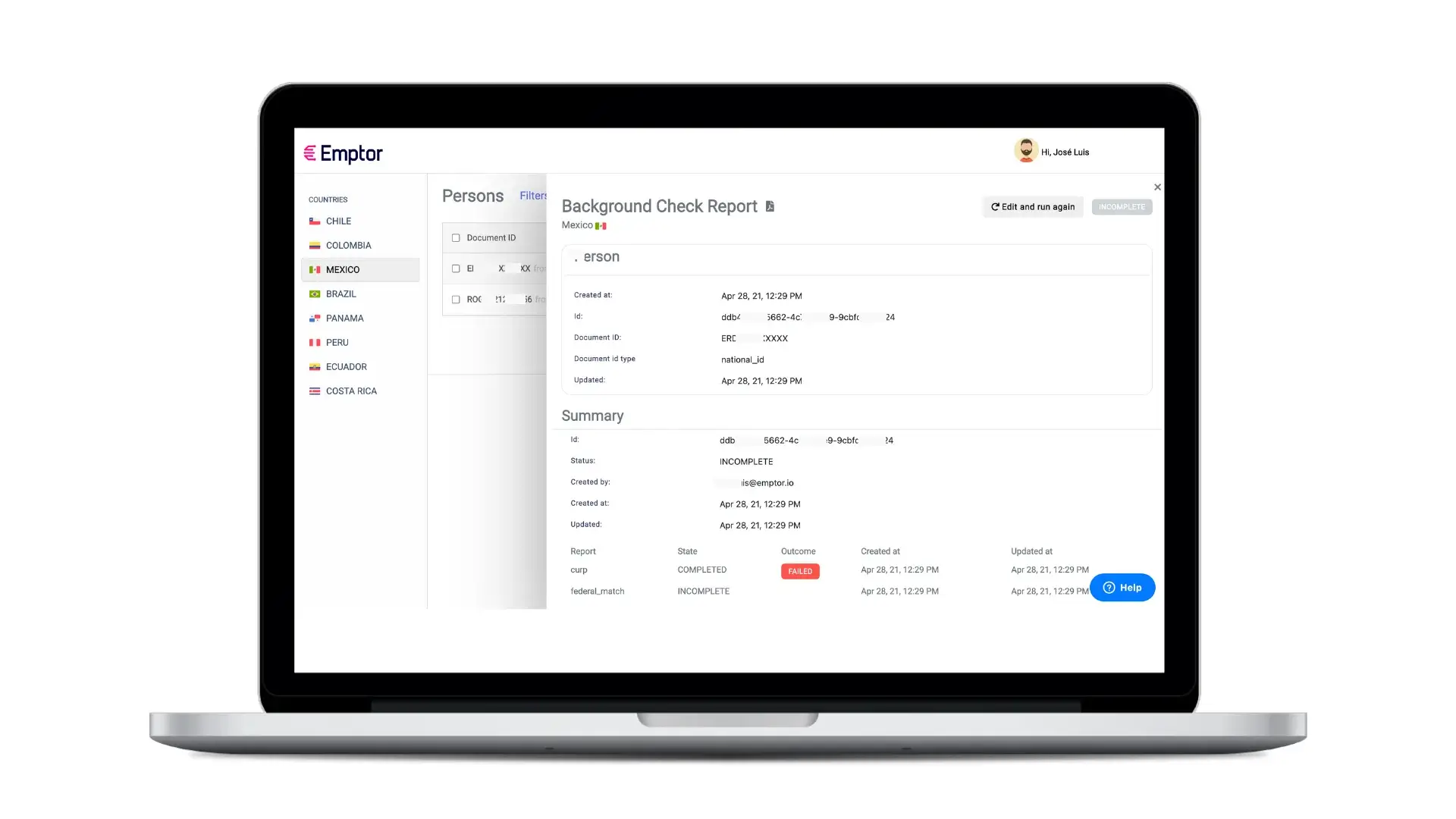 Automate validation of your candidates criminal background with Emptor's easy-to-use platform.
Automate validation of your candidates criminal background with Emptor's easy-to-use platform. With local expertise and regulation compliance with 8 countries in Latin America.
With local expertise and regulation compliance with 8 countries in Latin America.
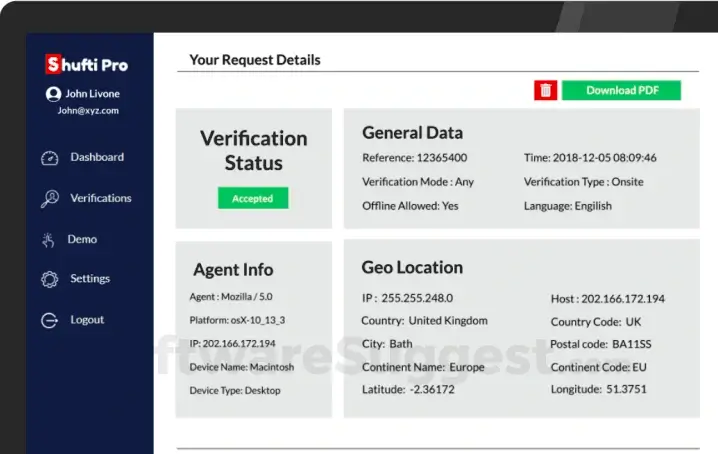 Shufti Pro is an AI-powered SaaS product that helps online businesses in identity theft protection, online fraud prevention, and payment scams.
Shufti Pro is an AI-powered SaaS product that helps online businesses in identity theft protection, online fraud prevention, and payment scams. Double up security protection from cybercriminals with Shufti Pro’s two factor authentication solution.
Double up security protection from cybercriminals with Shufti Pro’s two factor authentication solution.
 Boku empowers the new age of digital commerce with secure transactions.
Boku empowers the new age of digital commerce with secure transactions.
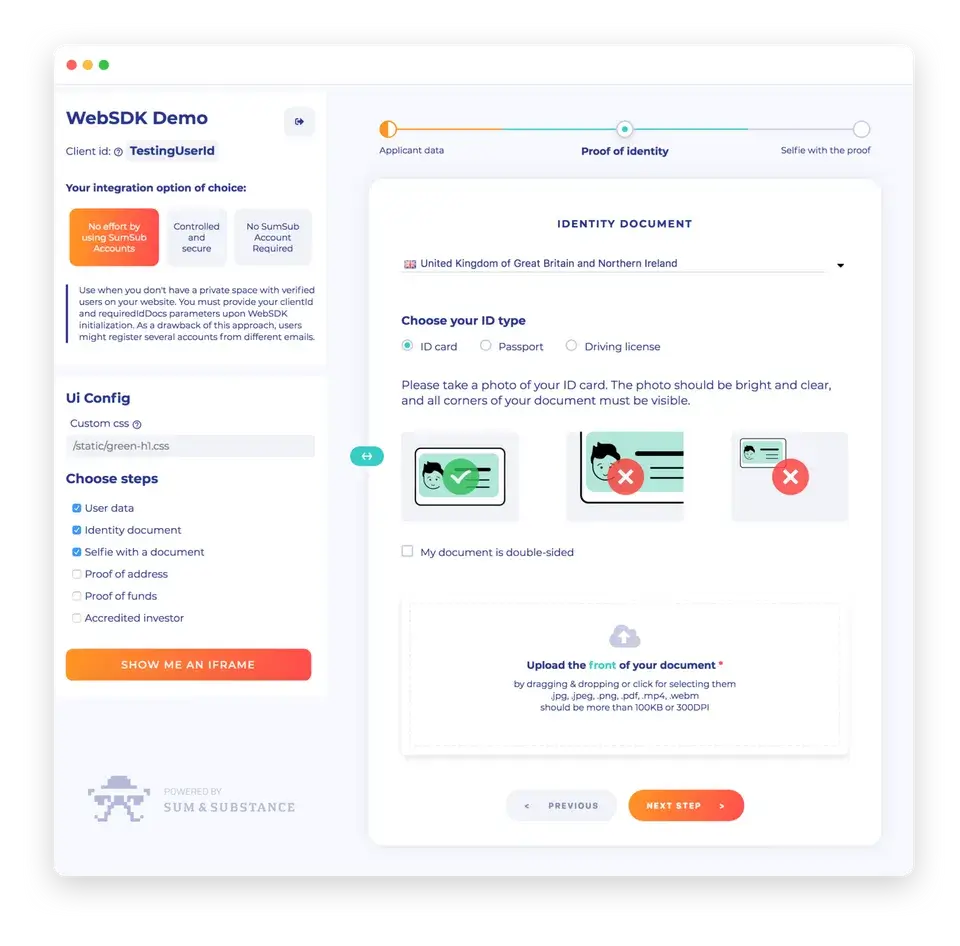 Protect various businesses from fraud and assure regulatory compliance with Sumsub's array of checks such as KYC, biometric authentication, document verification, and crypto compliance.
Protect various businesses from fraud and assure regulatory compliance with Sumsub's array of checks such as KYC, biometric authentication, document verification, and crypto compliance.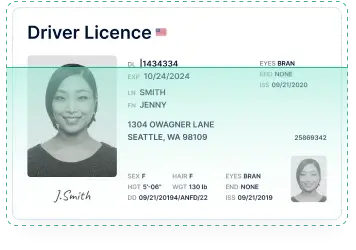 Tackle any proof of address document out there with Sumsub.
Tackle any proof of address document out there with Sumsub.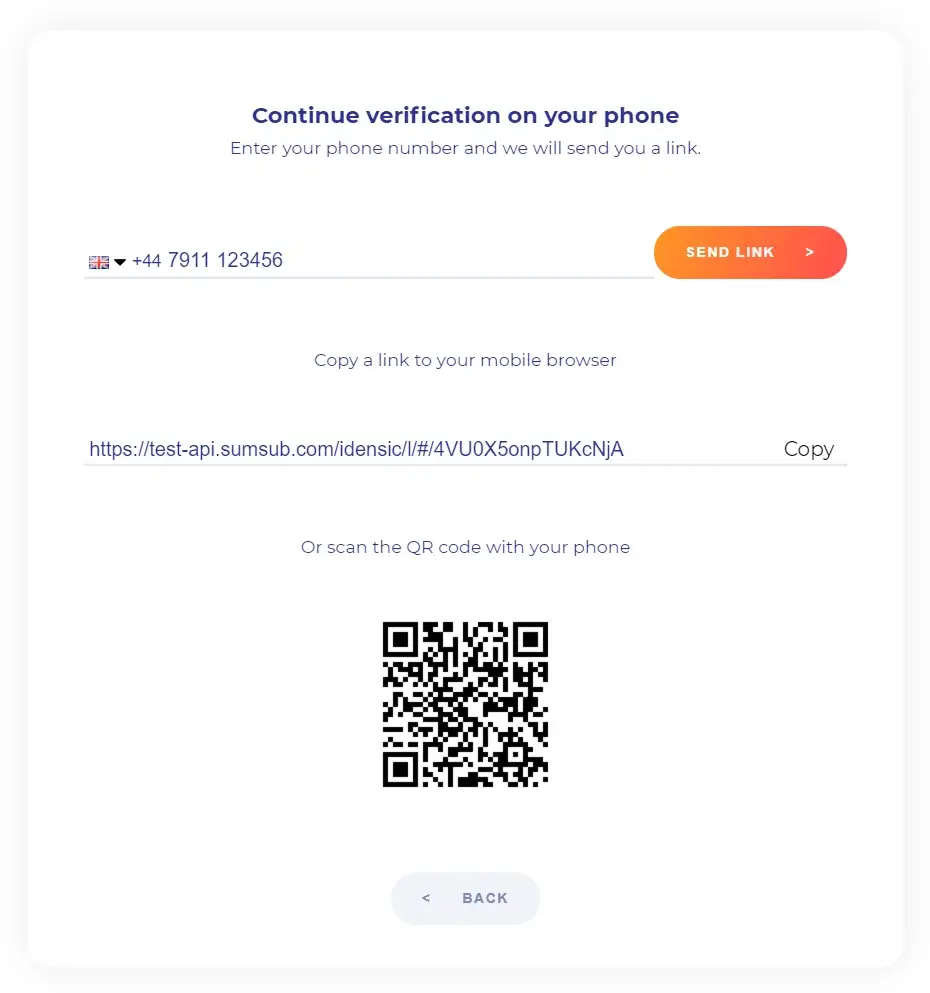 Validate email addresses & phone numbers to keep fake accounts out.
Validate email addresses & phone numbers to keep fake accounts out.
 Intellicheck can help against fraud and compliance problem.
Intellicheck can help against fraud and compliance problem.
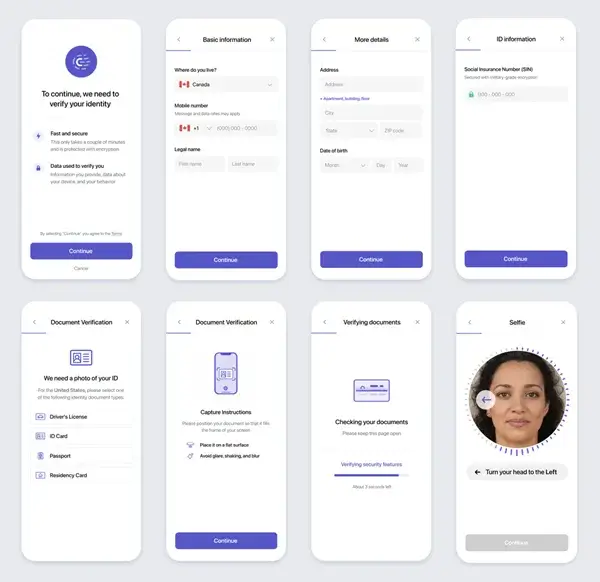 Cognito provides easy and comprehensive online ID verification services to customers.
Cognito provides easy and comprehensive online ID verification services to customers.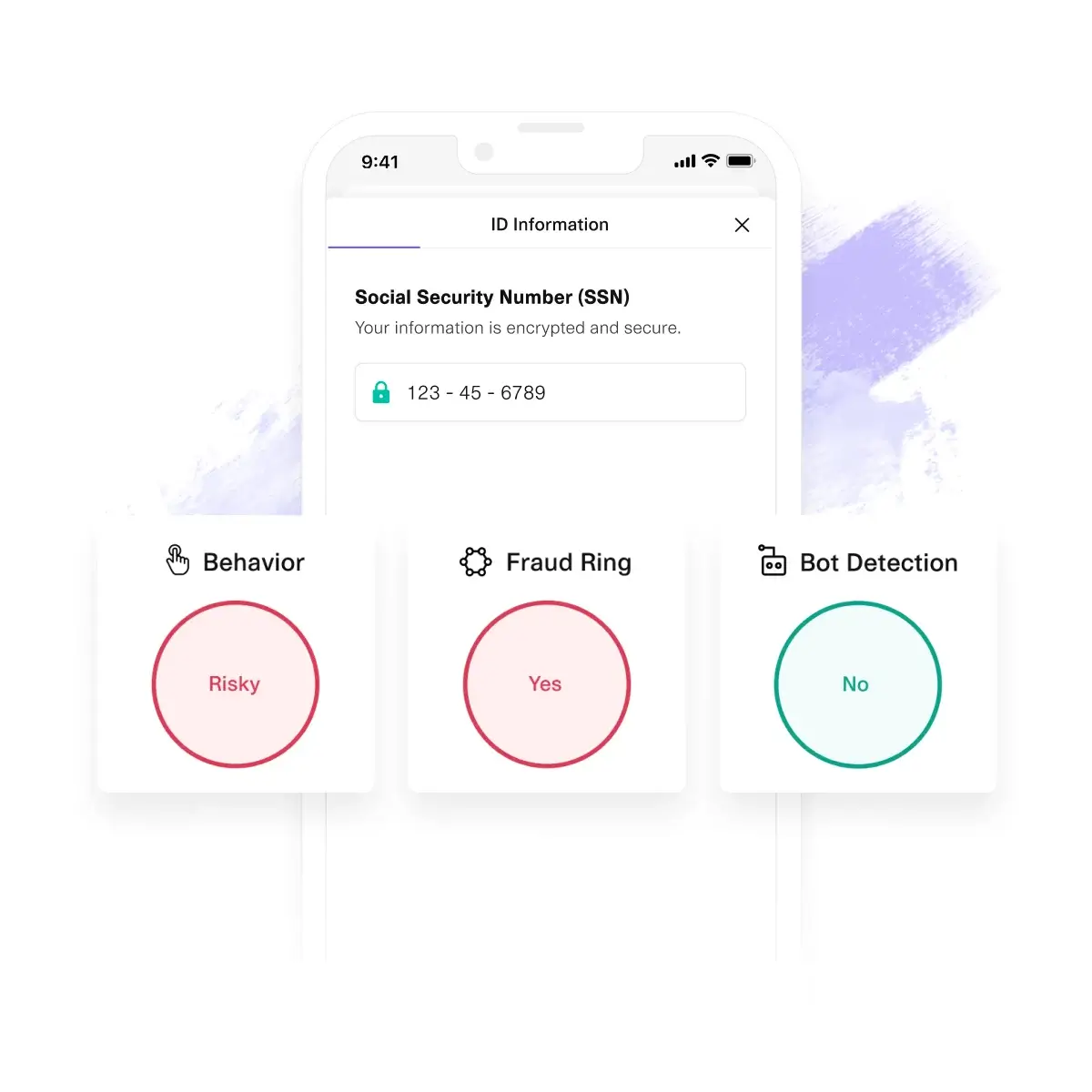 Detect and prevent bad actors from accessing your platform in real-time.
Detect and prevent bad actors from accessing your platform in real-time.
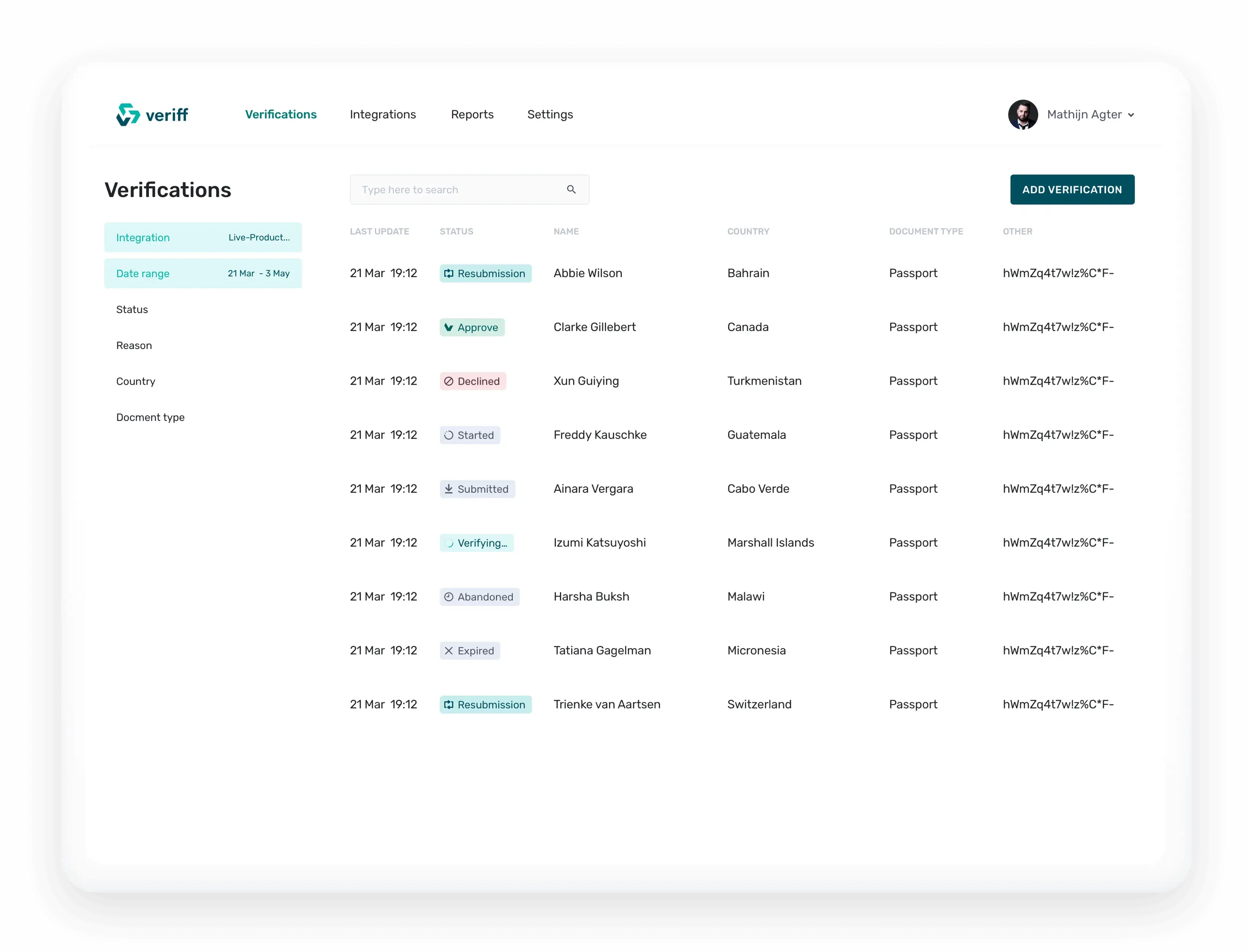 Veriff is the innovator in character check and KYC computerization and personality extortion counteraction.
Veriff is the innovator in character check and KYC computerization and personality extortion counteraction. Mitigate fraudulent activities with Veriff’s biometric authentication.
Mitigate fraudulent activities with Veriff’s biometric authentication.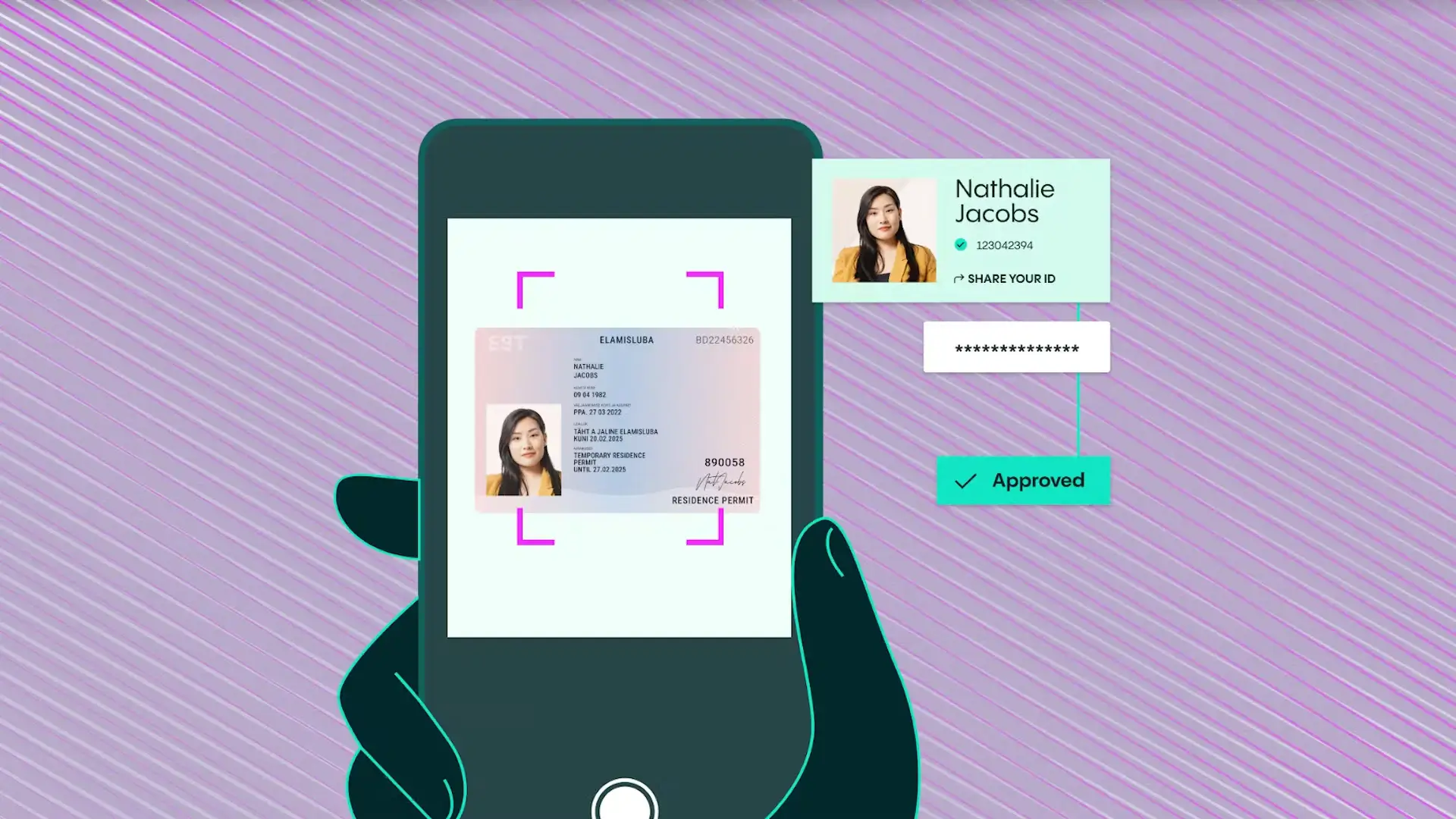 Strengthen security access by providing two different authentication factors in verifying identity.
Strengthen security access by providing two different authentication factors in verifying identity.
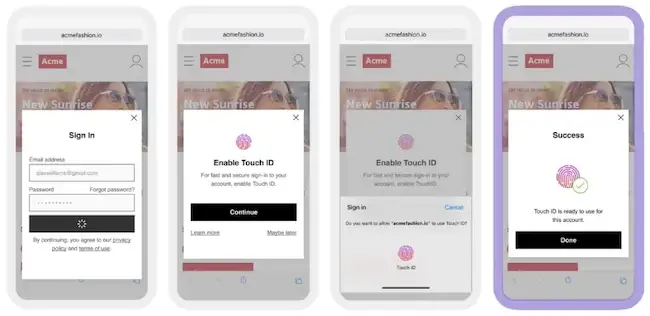 Improve business growth and profitability through a “tap and go” sign-in experience with Trusona.
Improve business growth and profitability through a “tap and go” sign-in experience with Trusona.
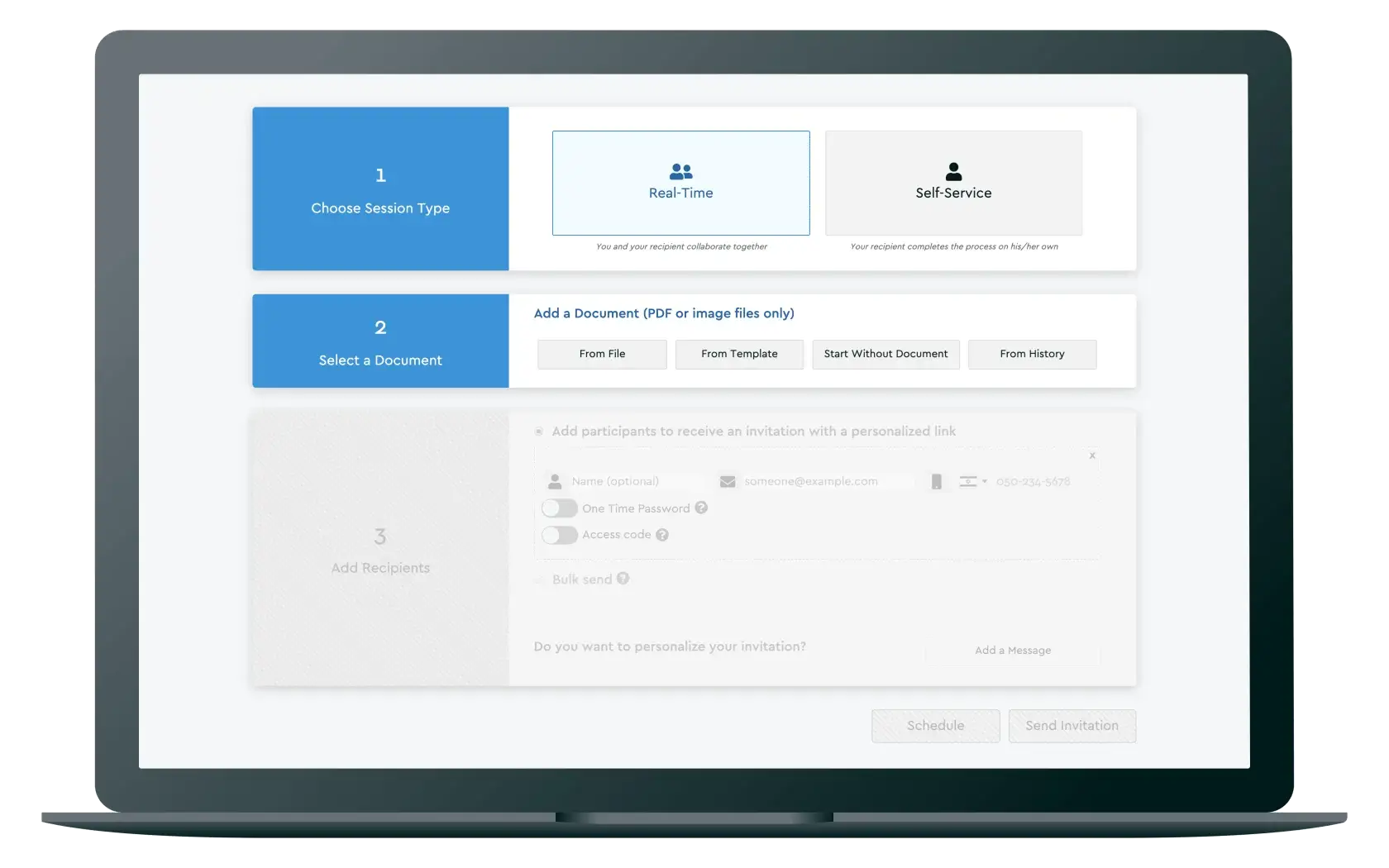 Document collaboration, web conferencing, and ID verification, all in one single platform.
Document collaboration, web conferencing, and ID verification, all in one single platform.